Summary of the Article
Have a project in mind?
Schedule a Call12 Best practices for web application security
Summary of the Article
Without a doubt, the Internet has completely revolutionized our world, and every business (either big or small) is shifting its business online.
The number of web applications is increasing, and so are the security threats. Many people don’t focus on the security of their online business, and such type of web apps allows hackers to compromise user’s data.
So it becomes vital for everyone to understand the importance of online security. There are different types of attacks the hackers can perform to compromise the security of your application and your user’s personal information. Some of the frequent attacks are –
- Cross-Site Scripting (XSS)
- SQL Injection
- DDoS Attack
- Malware
- Bots
- Cross-Site Request Forgery (CSRF)
- Broken Authentication
- Exploiting Inclusion Vulnerabilities – LFI and RFI
To give you the idea of the increasing threat, here are the industries most frequently targeted by DDoS worldwide –
Now, there is no chance that a web app can be 100% secure as some unforeseen circumstances can happen at, but there are some methods which every company should implement to reduce any chance of an attack.
So, we will be highlighting some key points which we implement in our client application to ensure proper security.
Best practices for web application security
Create a security blueprint
The biggest challenge being faced by any business is to keep up with the exponential growth in customer demands which are happening at the speed of lightning like new customer portals, simplified payment gateway solutions, new applications, etc.
To get new features out, companies do not follow an organized approach, or we can say that it is not a priority for them.
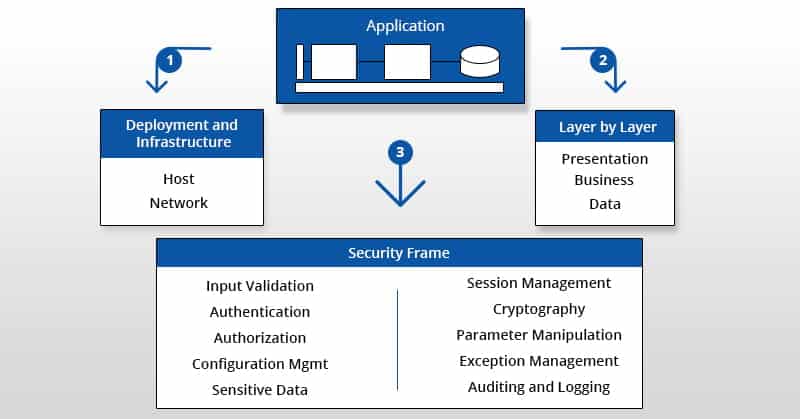
So to have a proper security plan in place, companies must have a blueprint of all the assets that are in use. It is like an inventory sheet where you update all the application details like 3rd party components, deployment mode, application layers, existing security methods, etc.
It will help in patching any vulnerability quickly and in a more efficient manner.
Assign priority tags to your inventory list
After you have created your inventory list the next logical step is to assign priority tags to the items in the list. With so many applications to fix, it is quite easy to list focus.
Without prioritizing, it will be challenging for you to choose which thing to focus on and thus you will struggle to make any progress in your task.
There are three priority tags you can assign to the items in the inventory list –
- Critical
The tag is assigned to those external modules which deal with customer and transactions data. Hackers will always attempt to target these modules so these should be tested and fixed with first priority.
- Serious
These can be both internal and external modules which may contain sensitive company information.
- Normal
These are the modules which have less exposure in the application or might not have direct access in the app. But these also need to be tested and fixed.
Analyze and prioritize all app vulnerabilities
After you have created the security blueprint and prioritize the modules for testing, the next step is to prioritize the list of vulnerabilities that you will start receiving when you start your testing out the modules.
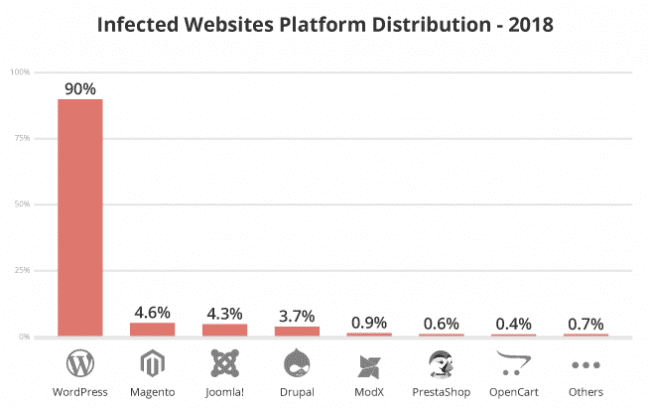
According to a report by Trustwave Global Security, an average application can have 20 vulnerabilities.
Sucuri after analyzing 9000 infected websites created a report and categorized them by the platform.
It is also evident that you can’t eliminate all the vulnerabilities from the application and it is not even worth the time, and also not all vulnerabilities will trigger a breach in your application, but it is essential to understand the priority of the vulnerability.
Vulnerabilities like Cross-site scripting, Injections, etc. are very dangerous and should be fixed on utmost priority.
You can check out OWASP top 10 vulnerabilities which provide an in-depth analysis of thread agents, weakness, technical impacts, etc.
Deploy initial protection
Finding any vulnerability in the application is not an easy task. It may take up weeks to find a weakness and months to fix that no matter whether your application is big or small.
According to a report by Web Application Security Statistics, fixing any vulnerability can take 146 days on average. Are you willing to wait that long?
Maybe you are, but the hacker will not wait. So in the meantime, you can apply some initial security measures on your application to prevent hackers from exploiting any weakness.
Introduce a Web Application Firewall
You can route the traffic on your application through a Firewall which will block any malicious activity. Some advanced Firewalls even support custom rules to prevent any exploitation. You should deploy a firewall to your application if you are facing a shortage of resources for risk management.
Restrict app functionality
If you don’t want to go with a Firewall and want to wait for all the vulnerabilities to fix, then you can limit the app functionality by restricting access to the database, sessions, etc. to prevent attacks.
Use cookies securely
The other area where an organization doesn’t focus that much is the use of cookies. It is very convenient to use cookies in your web applications as it offers the users faster visits to the application along with personalized content offerings. However, cookies can be easily manipulated by hackers to reveal sensitive information.
So you should make sure that you never store any sensitive or critical information such as passwords in the cookies.
Also, you should encrypt the information that is being stored in the cookies.
Other web application security measures
Update passwords frequently
The administrator passwords need to be changed periodically following the best practices in password structure & update frequency.
Proper session handling
A proper session handling must be maintained with appropriate session timeouts. Straight away dismiss multiple sessions from a single user.
Remove old applications
While you continue to improve your main application by introducing new applications, you certainly forget about some old applications that remain the part of your primary application but does not serve any purpose. These type of applications should be removed from the main application regularly.
Continuous monitoring
Setup proper continuous monitoring of your application that provides your a proper visibility into the vulnerabilities being targeted by hackers, where these attacks are coming from and what hackers do while attempting to exploit any vulnerability. This information helps in building a proper defense system to avoid any future attacks.
Proper log monitoring
Proper monitoring of error logs should be done regularly. If there has been any data breach or any attack, logs will help in finding out what went wrong. This data will help to prevent any future attacks and strengthen the infrastructure.
Summary
Keeping the user data secure has become a sensitive topic for all the organization whether it is big or small.
As your application grows, it becomes cumbersome for you to keep track of your application security. This is where you can hire a development partner who not even helps you in app development but also ensures that your application is secure and runs smoothly for your users.
We at VT Netzwelt ensures that your application is always up and running and free from any kind of vulnerabilities. We keep proper track of your application performance and have adequate security guides in place to tackle any unwanted situation.
We have achieved Top in the market tag, and that is only because of the quality services which we have offered to our clients. You can check out our client testimonials to understand the quality of work we have delivered.









test